// Video Solutions

VMS?
What’s New With
Learning the language and particularly the features of public clouds is essential, particularly the vast array of security features there.
IMAGE COURTESY OF MOTOROLA
What’s New With VMS?
The cloud, COVID-19 and technology advances have made video management systems more valuable than ever.
By Kathleen Hannon, SDM Contributing Writer
Capabilities in video management systems [VMS] are growing rapidly, in part thanks to the cloud and all the opportunities that the cloud affords to convert security video into actionable information that can improve not only security, but operations, customer service, and even marketing. The cloud offers a variety of built-in software solutions that make advancements less a choice of cost, and more a choice of allocating IT resources to meet a variety of customer needs.
We checked in to see what VMS suppliers are working on, and why. While the COVID-19 pandemic spurred manufacturers to shift focus to remote access and the ability to review company compliance with CDC health recommendations onsite, IoT and cloud-based business intelligence applications offer many more innovative possibilities going forward.
Surveillance Application Advancement
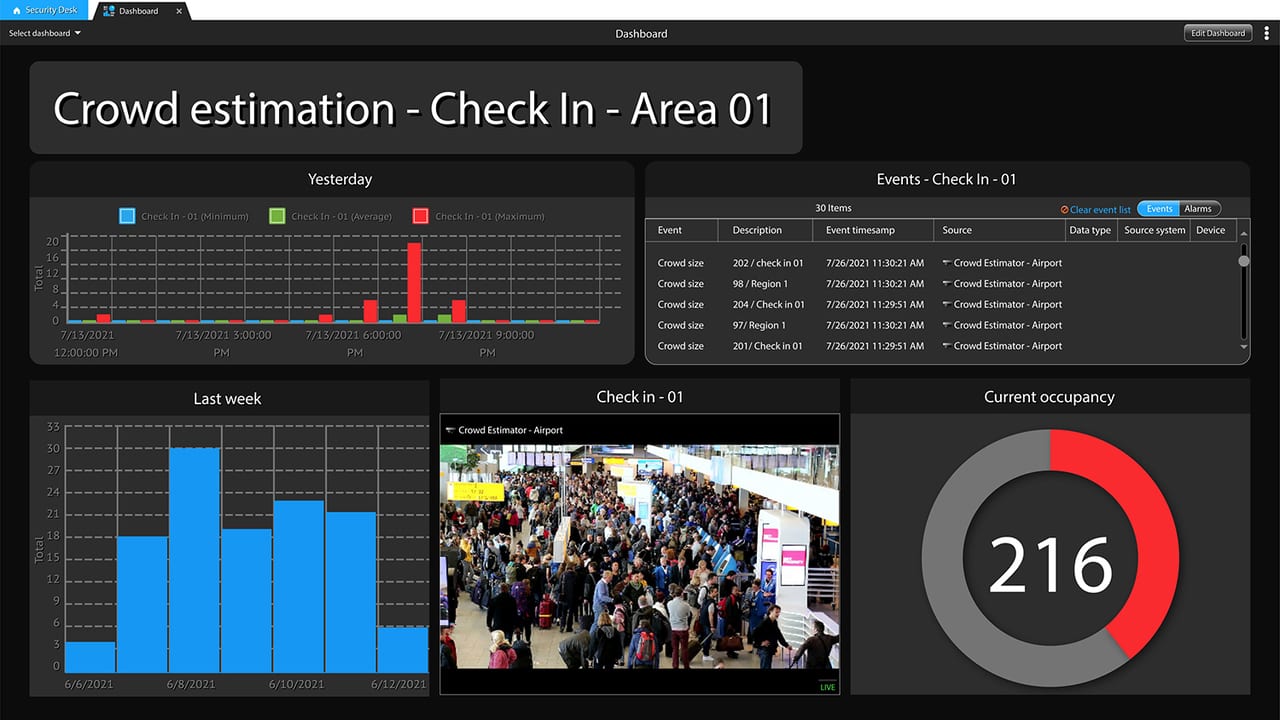
Genetec, Montreal, Quebec, has developed a crowd estimation application. “In the mall, or the airport, or even a business, customers want a notification when there are more than 50 people congregating in one area,” says Product Marketing Manager Laurent Villeneuve. “Our application provides an estimate in real time and you can either initiate an alarm or simply generate reports to leverage that data.”
Troy Wideman, regional marketing manager for Bosch Security Systems, Fairport, N.Y., says, “Our latest version offers map-based tracking assistance and improved geographical awareness with online maps to help operators pinpoint areas of interest, providing greater situational awareness, which enables a more informed response.”
Crowd estimation applications such as this one from Genetec have multiple applications for public areas.
IMAGE COURTESY OF GENETEC
Teledyne FLIR, Wilsonville, Ore., offers United VMS (UVMS), a scalable solution, says Kai Moncino, global business development manager for security. “[Features] include health monitoring to automate the process for finding faults early before critical issues arise, along with failover redundancy for maximum uptime,” he says.
Jason Burrow, Western regional sales manager for Coppell, Texas-based IDIS says his company’s solution suite includes voice relay. The company’s new real-time transport protocol (RTP) as a service enables seamless and stable video and voice relay to third-party devices and software with an SDK or API, increasing system flexibility and helping security teams coordinate responses to incidents and threats.
VMS Cybersecurity Post-Breach
Vulnerabilities exist in even the most seemingly impenetrable security systems, particularly when it comes to cybersecurity. A missed patch, a disgruntled employee, a phishing email, or even an infection from a customer’s undisclosed breach, can facilitate disaster. And every breach that affects one company can impact the industry as a whole. In March of this year, a well-known start-up VMS supplier was hacked when a super-admin user ID and password was publicly posted on the web. For 36 hours, hackers gained access to 150,000 security cameras inside multiple household brand-name companies. As the media carried the story on the front pages, it was a moment for the security industry to pause and reflect on their own best practices. So what were the takeaways?
Transparency was an overwhelming winner. Hanwha’s Aaron Saks says, “If there’s an issue, be transparent. Mitigate. Be immediate.”
Genetec’s Laurent Villeneuve agrees. “When you have a breach, the worst thing you can do is try to hide it, as that allows the breach to spread and cause maximum damage. We have strict policies of disclosing vulnerabilities and potential vulnerabilities to clients within 72 hours of detection.”
Dr. Carl Elks, a Ph.D. in Computer Engineering at Virginia Commonwealth University specializing in safety and security says, “In every cybersecurity breach, you want your defense to be more powerful than the offense. When you try to hide a breach, the offense — the hackers — know. They have the advantage as they can leverage your secrecy against you.”
Elks regards breaches as an inevitability. “An R&D team is a finite number of people developing your cybersecurity strategy, while customer access will likely number in the millions. At least one will find or create a vulnerability, even if innocently. A conceptual change in cybersecurity posture is both occurring and necessary: Stop thinking of cybersecurity exclusively as perimeter security. Assume a bad actor is going to get in. Start thinking of systemic security where there is containment in terms of the information that bad actor can access once inside.”
//
Artificial Intelligence Development
There’s nothing quite as resource-taxing as having a security team watch hours and hours of footage to find a lone object or individual, let alone the fact that these searches typically have some measure of urgency attached. Artificial intelligence (AI) capabilities are paving the way to achieving that goal.
“We’re investing a lot in AI,” says Austin, Texas-based Eagle Eye Networks’ CEO Dean Drako. “While approximately 95 percent of AI elsewhere is implemented utilizing on-prem servers, that limits the ability to manipulate the data, so we are merging our AI technology with our VMS and building it into one cloud solution where you can search video with a command-line interface for best matches. With our latest advances, you can check vehicles for license plates, parking, direction they were moving. There are traditional security applications as well. It’s handy in [detecting] slip and fall incidents, intrusion, or vandals.”
IDIS’ new real-time transport protocol (RTP) as a service enables seamless and stable video and voice relay to third-party devices and software with an SDK or API, increasing system flexibility and helping security teams coordinate responses to incidents and threats.
IMAGE COURTESY OF IDIS

Hanwha Techwin America Senior Product and Technical Training Manager Aaron Saks says his company is emphasizing AI as well. “Our current VMS Wisenet WAVE does a smart search and sees motion or movement. We can detect people’s faces, objects, colors, and then do analytics. We can search for an object from a simple command line [such as] ‘Do a search for a blue car.’ It saves hours of watching video. You get a hit within seconds.”
Motorola Solutions, Chicago, is also working on AI, with a focus on tracking a person of interest, says Vice President of Development Hamish Dobson. It allows users to look at live video of a PoI and see where they came from and went. “Right click on the video and using an AI scan you can follow them throughout the system … purely based on their personal description,” he explains.
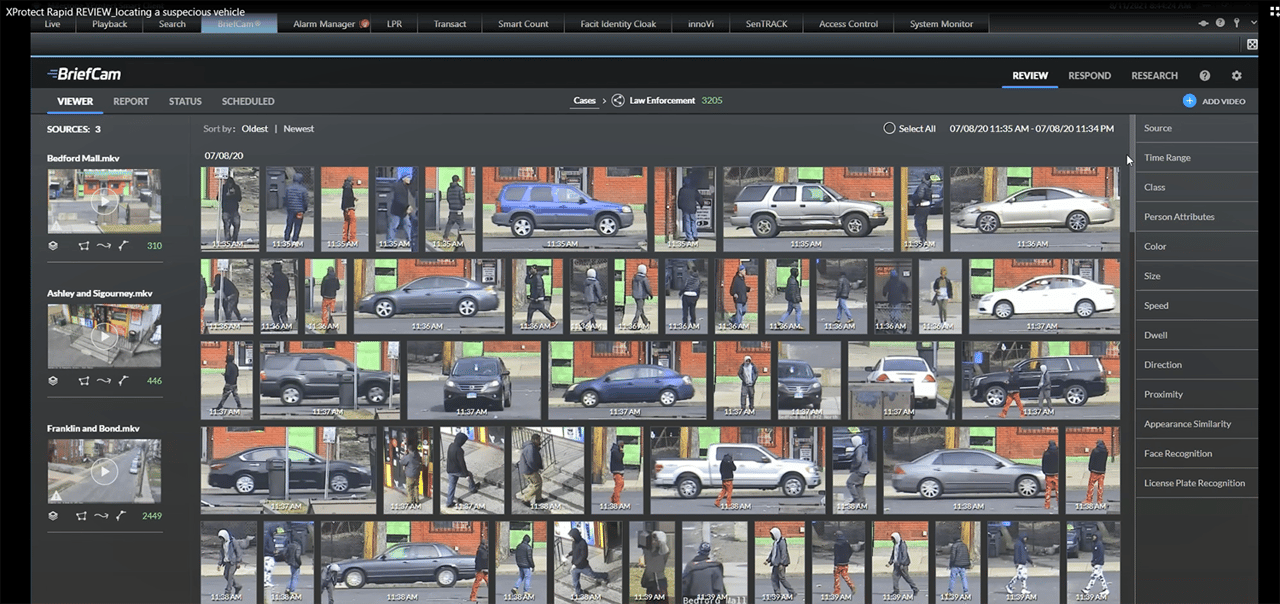
Milestone’s XProtect Rapid Review is available as an add-on that is seamlessly integrated into the XProtect VMS Smart Client, says Jennifer Hones, manager, key account team, Milestone Systems, Lake Oswego, Ore. “It is an intelligent video analytics solution that allows security operators and investigators to efficiently search vast amounts of video recordings and pinpoint exactly what they are looking for in minutes.”
Integrating VMS Within the Security Platform
Other manufacturers are working on deeper integrations within their video management systems.
“Our SecurOS 11 Video Intelligence Platform provides video management and native video analytics for small to large-scale security applications,” says Aluisio Figueiredo, CEO of Intelligent Security Systems (ISS), Woodbridge, N.J. “The platform is available as an end-to-end solution running on ISS network video servers, and has existing integrations with most third-party security systems such as access control, fire alarm, building management and more.”
Panasonic i-Pro’s latest upgrade, Video Insight, offers a fully integrates i-PRO’s MonitorCast access control platform to deliver uncompromised system management and control with unlimited scalability on a unified platform.
IMAGE COURTESY OF PANASONIC I-PRO

Optimizing Planning & Scalability
The old saying goes, “If you don’t make mistakes, you don’t make anything.” Recognizing there’s always room for everyone to improve, what do suppliers see as the most common mistake that integrators make?
The most pervasive answer was inadequate planning. Suppliers have noticed a surge in hardware and software choices that are either incompatible with one another, or do not match the individual customer’s need to scale. The shift is likely a natural by-product of the change from integrators recommending products to customers choosing their products before their integrator.
“[Recognizing] the inability of a VMS to easily integrate with other systems and devices without the need for costly, custom integrations typically arises when a customer looks to enhance their system in scale or capabilities, and the VMS software they have in place limits or completely restricts them from doing so,” says Panasonic I-Pro’s Adam Lowenstein.
Vicon’s Aliyah Picanso agrees. “While there are often similarities in the competitive landscape of physical security solutions, there are also subtle differences that can cost additional time and labor as technicians juggle multiple platforms. Simple things like camera discovery tools can trip up even the most seasoned integrators.”
IDIS’ Jason Burrows’ concern is selling the customer more than they need. “End users are waking up to the high ongoing OPEX costs and bundled packages from established players that they don’t even use. Integrators need to consider giving the users functionality they need most by thoroughly considering needs site-by-site, as they can vary vastly.”
//
Adam Lowenstein, director of product management for Panasonic i-PRO Sensing Solutions Corporation of America, Rolling Meadows, Ill., says the company’s latest upgrade, Video Insight, offers a “powerful, easy-to-use enterprise VMS platform ... that fully integrates i-PRO’s MonitorCast access control platform to deliver uncompromised system management and control with unlimited scalability on a unified platform.” This functionality includes monitoring, mobile, health monitoring, and more, he adds.
Aliyah Picanso, product marketing manager for Vicon, , Hauppauge, N.Y., says her company’s latest platform updates include “sophisticated alarm management options, a new integration framework, improvements to the health dashboard and more.”
Many of the systems also include real-time direction to incident teams on the ground to ensure best practices.
“VMS is no longer only used for video playback and recording, but also must have the capability to consolidate information from numerous systems. Customers want security systems to be intelligent, with the ability to identify and notify anomalies that can occur on all operational cameras simultaneously.” Figueiredo says. “At ISS, we are experiencing a sharp increase in requests for sophisticated solutions that are proactive solutions for a wide range of physical security and business intelligence applications.”
Opportunities for Security Integrators
Cloud capabilities, IoT, and AI are some of the top technology trends in VMS, but one of the most commonly mentioned trends manufacturers note is not technology-related, but rather how customers are taking first chair. “In the old world, end users would call a local integrator, and the integrator would recommend the products and do the install,” Eagle Eye’s Drako says. “Now the product is being more heavily dictated by the customer because they want scalable, global consistency: one user interface, one maintenance schedule, one security posture. That’s not easily achieved under the old model, because regional integrators would recommend and use disparate systems.”
AI enables security operators to efficiently search vast amounts of footage within minutes.
IMAGE COURTESY OF MILESTONE
For many integrators, the trend away from installations as the base of their business model to a software-based recurring revenue model (RMR) potentially means a major but positive change in the eyes of VMS manufacturers. Instead of the ‘one-and-done’ installation business model that obligates integrators to always sell more and newer hardware, the RMR-based model offers integrators a deeper, more enduring relationship with their customers as a support service in terms of customization, monitoring, and training.
“This shift can be real opportunity to expand their business,” says Genetec’s Villeneuve. “Being hybrid is a good business model.”
But when it comes to expanding their subject matter expertise, where should integrators focus their efforts
Motorola’s Dobson says, “Learning the language and particularly the features of public clouds is essential, particularly the vast array of security features there, as some customers have concerns. AI and analytics are another core area, as there are a lot of capabilities that aren’t well understood. Integrators can educate their customers on what is possible with the analytics — how to customize workflows and use the amazing search tools.” SDM
